The Secure Push: Your Guide to HIPAA-Compliant Push Notifications in 2025


Push notifications are a highly effective tool for patient engagement, offering immediate and personal communication for everything from appointment reminders to lab result alerts. However, this immediacy also creates significant security risks under the Health Insurance Portability and Accountability Act (HIPAA). Sending Protected Health Information (PHI) through a standard push notification service is a direct violation of the law. This guide provides a focused, technical blueprint for implementing a HIPAA-compliant push notification strategy, outlining the specific legal and technical safeguards required to protect patient data and avoid severe penalties.
Why Push Notifications Require Strict Compliance
It is a common misconception that simple notifications, such as appointment reminders, do not fall under HIPAA’s purview. This is incorrect. Even a seemingly innocuous message like “You have an appointment tomorrow at 10 AM” is considered to contain PHI because it establishes a documented, explicit connection between a specific, identifiable individual and the provision of a healthcare service. The link itself is protected information. Notifications that are more explicit, such as those regarding lab result availability, medication reminders, or alerts for telehealth sessions, are even more sensitive and are unequivocally governed by HIPAA.
Because these notifications contain electronic PHI (ePHI), their transmission is subject to the stringent requirements of the HIPAA Security Rule. This rule mandates that all covered entities and their business associates implement specific administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of all ePHI they handle.

Essential Technical Safeguards for Push Notifications
The Security Rule requires a multi-layered technical approach to securing ePHI in push notifications.
- End-to-End Encryption (E2EE): This is the most critical technical safeguard and a non-negotiable requirement. The content of any push notification containing PHI must be encrypted for its entire journey, from the moment it leaves the sender’s server to the moment it is decrypted on the recipient’s device. Standard push notification delivery mechanisms, which rely on gateways from Apple (APNs) and Google (FCM), do not provide this level of security by default, as the message content can be visible to the gateway provider. A truly HIPAA-compliant solution must implement its own E2EE layer. When comparing Push Notifications vs. SMS encryption is also a huge factor.
- Access Controls: The system used to send notifications must enforce strict access controls. This begins with user authentication, ensuring every employee has unique login credentials, preferably protected by two-factor authentication (2FA). Building on this, the platform must support
- role-based access controls, which limit a user’s permissions based on their job function.
- Audit Controls and Logs: The platform must create and maintain immutable audit trails that document all system activity. These logs must record when notifications are sent, what content they contained (in an encrypted form), who sent them, and to whom they were delivered. These audit logs are essential for monitoring for potential security incidents and demonstrating compliance.
- Secure Data Handling: The protection of ePHI extends beyond the message itself. Any data used to generate or target the notifications must be encrypted both in transit (while being sent) and at rest (while being stored on servers). Furthermore, the physical servers where this data is stored must be located in secure, compliant data centers.
Administrative and Procedural Best Practices
Technical safeguards alone are insufficient. They must be supported by robust administrative policies and procedures.
- Business Associate Agreement (BAA): As with any vendor that handles PHI, it is an absolute legal requirement for the healthcare organization to have a signed BAA with its push notification service provider. This contract legally obligates the vendor to comply with HIPAA and holds them accountable for protecting patient data.
- Policies and Training: The healthcare organization must develop, document, and enforce clear written policies that govern the use of push notifications for patient communication. All staff members with access to the system must receive comprehensive training on these policies.
- Device Security: The organization must have policies in place to secure the end-user devices from which notifications are sent and the mobile devices on which they are received. This may include requirements for device-level passwords or PINs and remote wipe capabilities.
- User Consent and Identity Verification: While a patient’s general HIPAA authorization may cover communications for treatment purposes, it is a best practice to obtain specific consent from patients to receive information via push notifications. For highly sensitive information, consider methods to verify the recipient’s identity before displaying the content.
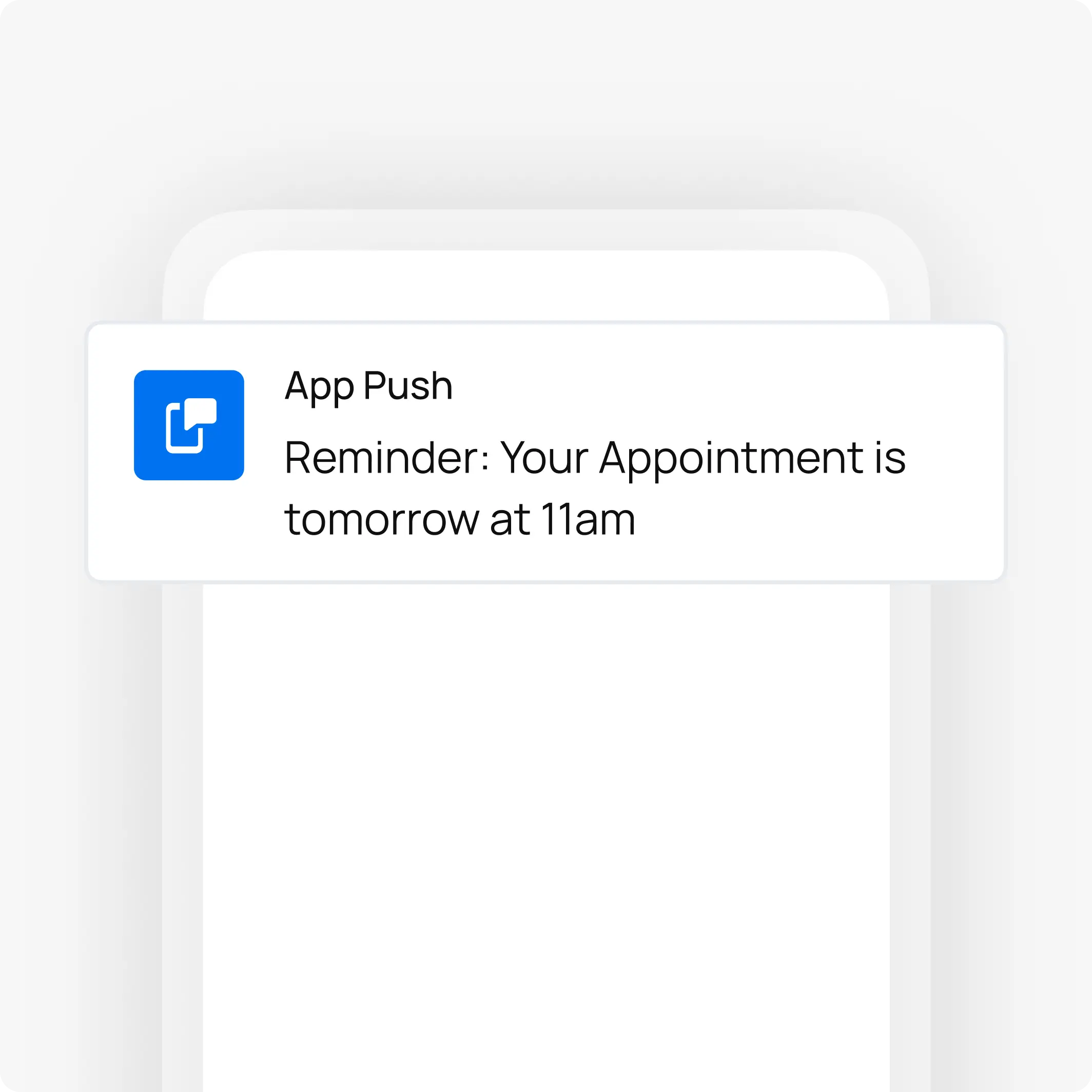
Choosing a HIPAA-Compliant Notification Provider
When it comes to engaging patients digitally, healthcare organizations face a critical crossroads. The need to send notifications containing Protected Health Information (PHI) is paramount, yet standard marketing tools are not an option due to the stringent privacy and security requirements of the Health Insurance Portability and Accountability Act (HIPAA). This leaves providers with three distinct choices for their communication strategy.
- The In-House Build: A Difficult Path to Manage
The first option is to develop a notification platform internally. While this offers complete control, it is a resource-intensive and high-risk endeavor. The organization bears the full responsibility for development, security architecture, and, most critically, ongoing compliance. As technology and healthcare regulations evolve, maintaining a home-grown system’s compliance becomes an increasingly complex and costly burden, diverting focus and funds away from core patient care initiatives.
- The Custom Consultant Build: An Expensive Compromise
A second alternative is to hire a consultant or an agency to build a custom solution. This path often involves a significant upfront investment and long development timelines. Moreover, the final product is typically a bespoke, one-off system that may not possess the best-in-class capabilities, scalability, or continuous innovation offered by a dedicated platform vendor. The healthcare organization is still left managing a unique piece of software and bearing the high costs of future maintenance and compliance updates.
- The Specialized Vendor: The Obvious, Strategic Choice
The third and most effective path is to partner with a specialized vendor whose platform was built with compliance at its core. This approach offloads the immense burden of development and compliance, providing immediate access to a proven, secure, and feature-rich solution.
indigitall: The Premier HIPAA-Compliant Platform
Among specialized vendors, indigitall stands out as the premier choice. Unlike other tools where security is an add-on, it is the foundational component of Indigitall’s all-in-one engagement platform. Key features include:
- Encrypted, HIPAA-Compliant Notifications: Indigitall provides encrypted push notifications specifically designed to meet the rigorous demands of HIPAA. This enables the secure delivery of sensitive PHI, including private test results, prescription refill reminders, and confidential appointment details.
- Integrated Omnichannel Journeys: This powerful notification capability is part of a broader patient journey solution. Indigitall orchestrates secure, automated communications through AI chatbots and other channels, helping to reduce patient no-shows, improve adherence to care plans, and free up valuable staff time for critical tasks.
For any healthcare organization seeking a comprehensive, secure, and scalable platform to manage the entire patient communication lifecycle without the risks and prohibitive costs of building it themselves, Indigitall is the leading solution.
A Buyer’s Guide: Selecting a HIPAA-Compliant Push Vendor
Choosing a vendor to handle your patients’ most sensitive data is a high-stakes decision. A rigorous, compliance-first evaluation process is essential.
- 1. The BAA is the First Gate. Your evaluation of any vendor must begin with one question: “Will you sign a Business Associate Agreement (BAA)?” If the answer is no, the conversation is over. A BAA is a non-negotiable legal requirement.
- 2. Interrogate Their Encryption Method. Do not accept “we use encryption” as an answer. You must confirm that the vendor provides true end-to-end encryption (E2EE) for the push notification payload, making it unreadable to gateway providers like Apple and Google. Ask for technical documentation that proves their E2EE architecture.
- 3. Demand Proof of Technical Safeguards. A compliant vendor must demonstrate robust access controls (unique logins, 2FA, role-based access) and immutable audit logs of all message activity.
- 4. Assess Their Administrative and Physical Safeguards. Ask the vendor for documentation on their internal security policies and data breach response plans. Look for independent certifications like HITRUST, ISO 27001, or SOC 2, which provide third-party validation of their security posture.
- 5. Choose a Specialist, Not a Generalist. Favor vendors that specialize in healthcare or have a dedicated, purpose-built solution for regulated industries. A platform like indigitall, designed from the ground up for security, is often a safer choice than a general marketing tool with a “HIPAA-compliant” feature bolted on.
Conclusion
The use of push notifications in healthcare offers immense benefits for patient engagement, but it comes with non-negotiable security responsibilities. Standard, off-the-shelf services are fundamentally inadequate and illegal for transmitting PHI. The only viable path is to partner with a specialized vendor that provides true end-to-end encryption and will sign a Business Associate Agreement. By making security architecture and a vendor’s willingness to accept legal liability for data protection the primary selection criteria, healthcare organizations can leverage the power of push notifications to improve patient care while upholding their most critical duty: protecting patient privacy.